In my previous blog post I showed you how to connect your Azure Container Registries with Azure Security Center.
-> https://www.danielstechblog.io/connecting-azure-container-registry-with-azure-security-center/
Today we talk about how to receive the scan results via Azure Resource Graph instead of using the Security Center UI path.
You can submit your queries against the Resource Graph via the Azure portal, Azure PowerShell, Azure CLI or the REST API.
I am using the Azure CLI in the following examples querying the scan results.
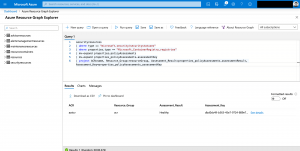
az graph query -q ' securityresources | where type == "microsoft.security/securitystatuses" | where properties.type == "Microsoft_ContainerRegistry_registries" | mv-expand properties.policyAssessments | mv-expand properties_policyAssessments.assessmentKey | project ACR=name, Resource_Group=resourceGroup, Assessment_Result=properties_policyAssessments.assessmentResult, Assessment_Key=properties_policyAssessments_assessmentKey ' | jq .
[
{
"ACR": "azstcr",
"Assessment_Key": "dbd0cb49-b563-45e7-9724-889e799fa648",
"Assessment_Result": "High",
"Resource_Group": "acr"
}
]
As seen above I get an overview about my ACR, the severity level and the assessment key. The latter one is used in the next query to get even more details about the scan result.
az graph query -q '
securityresources
| where type == "microsoft.security/assessments"
| where id has "'${ASSESSMENT_KEY}'"
| project Severity=properties.metadata.severity,
Implementation_Effort=properties.metadata.implementationEffort,
User_Impact=properties.metadata.userImpact,
Threats=strcat_array(properties.metadata.threats, ", "),
Link=strcat("https://",properties.links.azurePortal)
' | jq .
[
{
"Implementation_Effort": "Moderate",
"Link": "https://portal.azure.com/#blade/Microsoft_Azure_Security/RecommendationsBlade/assessmentKey/{REDACTED}",
"Severity": "High",
"Threats": "DataExfiltration, DataSpillage, AccountBreach, ElevationOfPrivilege",
"User_Impact": "Low"
}
]
Additionally, to the severity level I get information about the implementation effort as well the user impact. But the most important part is the URL to the finding in the Azure Security Center.
az graph query -q '
securityresources
| where type == "microsoft.security/assessments/subassessments"
| where id has "'${ASSESSMENT_KEY}'" and isnotnull (properties.id)
| mv-expand properties.additionalData.cve
| mv-expand properties.additionalData.vendorReferences
| project Time_Generated=properties.timeGenerated, Severity=properties.status.severity, ID=strcat_array(split(properties_additionalData_cve.link, "=", 1),""),
Patchable=properties.additionalData.patchable, Issue=properties.displayName, Remediation=properties.remediation,
Image=properties.additionalData.repositoryName, Digest=properties.additionalData.imageDigest,
CVE=properties_additionalData_cve.link, Vendor=properties_additionalData_vendorReferences.link
' | jq .
[
{
"CVE": "http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-18276",
"Digest": "sha256:593bb031b4cec71aaf6d6f19657b04aaf38e6feb77de3632dca2ae0d60b86441",
"ID": "CVE-2019-18276",
"Image": "akscnicalc",
"Issue": "GNU Bash Privilege Escalation Vulnerability for Debian (Zero Day)",
"Patchable": false,
"Remediation": "No updates available for Debian platform till date.",
"Severity": "High",
"Time_Generated": "2020-03-19T20:28:51.216Z",
"Vendor": "https://security-tracker.debian.org/tracker/CVE-2019-18276"
}
]
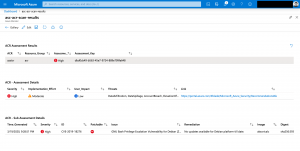
Running one more query with the assessment key on another table shows the interesting details about the issue, the corresponding CVE number as well information about the remediation.
Beside that you get the name of the affected container image repository with the image digest.
The queries above can be integrated into an Azure Workbook. So, you get again a graphical UI in the Azure portal. But only with the necessary information for you and your team.
You find the Azure Workbook as Gallery or Azure Resource Manager template on my GitHub repository.
-> https://github.com/neumanndaniel/armtemplates/tree/master/workbooks