Writing and evaluating Gatekeeper policies can be hard sometimes. Especially the testing part of a newly created policy.
There are different approaches to tackle this like having a dedicated test Kubernetes cluster for it. An alternative we used was a script starting a single node KinD cluster on Docker for Mac and installing Gatekeeper onto it.
The advantage of this approach you see how the policy works under real conditions. The disadvantage is properly the long feedback loop until the policy works as expected. Especially when you write complex policies.
Rego Playground
Here comes the Rego Playground into play. It is a web service that lets you easily evaluate your written policy.
-> https://play.openpolicyagent.org/
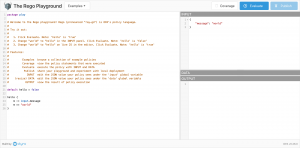
As seen in the screenshot on the left-hand side you put your Gatekeeper policy. You do not paste the whole ConstraintTemplate into the field just the part in the template after rego: |.
apiVersion: templates.gatekeeper.sh/v1beta1
kind: ConstraintTemplate
metadata:
name: k8sdisableautomountserviceaccounttoken
spec:
crd:
spec:
names:
kind: K8sDisableAutomountServiceAccountToken
targets:
- target: admission.k8s.gatekeeper.sh
rego: |
package k8sdisableautomountserviceaccounttoken
missing(obj) = true {
not obj.automountServiceAccountToken == true
not obj.automountServiceAccountToken == false
obj.serviceAccount == "default"
}
violation[{"msg": msg}] {
p := input_pod[_]
missing(p.spec)
msg := sprintf("automountServiceAccountToken field is missing for pod %v while using Service Account %v", [p.metadata.name, p.spec.serviceAccount])
}
violation[{"msg": msg, "details": {}}] {
p := input_pod[_]
p.spec.automountServiceAccountToken
p.spec.serviceAccount == "default"
msg := sprintf("Service Account token automount is not allowed for pod %v while using Service Account %v, spec.automountServiceAccountToken: %v", [p.metadata.name, p.spec.serviceAccount, p.spec.automountServiceAccountToken])
}
input_pod[p] {
p := input.review.object
}
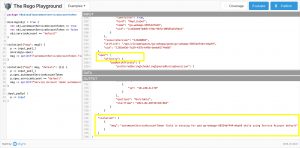
On the right-hand side in the upper part, you paste your input object as JSON. This can be for instance the output of an existing pod in your Kubernetes cluster.
kubectl get pods go-webapp-58554df444-mkph9 -o json
The reference to the input object for Gatekeeper on Kubernetes is input.object.review.
When pasting the JSON output for our pod into the Rego Playground as input we adjust the reference to the input object to just input.
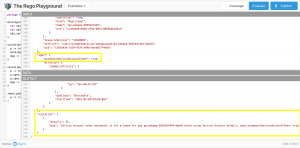
After that is done a click on Evaluate validates the input against the policy.
You get the results on the right-hand side directly underneath of the input section.
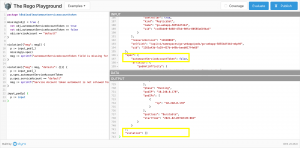
Looking at the screenshot the pod violates the policy. One small adjustment to the input object later it passes the policy.
Summary
The Rego Playground makes the writing of Gatekeeper policies a breeze. You get a fast feedback loop without spinning up a local KinD cluster or having a test Kubernetes cluster in place.