Last week I showed you the kubeconfig credentials distribution for AKS Engine.
-> https://www.danielstechblog.io/distribute-aks-engine-kubeconfig-credentials/
In this blog post I walk you through the steps for Azure Kubernetes Service.
The distribution of the kubeconfig credentials for an AKS cluster with AAD integration is a lot easier thanks to the following two built-in RBAC roles.
-> Azure Kubernetes Service Cluster Admin Role
-> Azure Kubernetes Service Cluster User Role
The cluster admin role lets you bypass the AAD integration and hence should be treated as an emergency or break glass account. You shall use this kubeconfig credentials only once, when creating the ClusterRoleBinding for the AAD group assigning the cluster-admin permissions for further management operations.
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: azst-aks-cluster-admins
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: Group
name: "{AAD GROUP OBJECT ID}"
For all other purposes you use the cluster user role to leverage the AAD authentication mechanism.
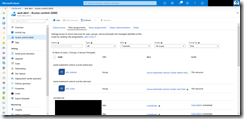
But let us step back. First, we need to add two role assignments at least to our AKS cluster object. One for the cluster admin role and one for the cluster user role to be able to retrieve the respective kubeconfig credentials.
As seen in the screenshot I have used two different AAD groups.
The only two requirements that our engineers and developers must fulfill are the following ones. Being a member of the AAD group with the cluster user role assignment and having the Azure CLI installed on their local workstation. Then they can get the kubeconfig credentials in a self-service manner via the Azure CLI.
> az login > sudo az aks install-cli --verbose Downloading client to "/usr/local/bin/kubectl" from "https://storage.googleapis.com/kubernetes-release/release/v1.15.1/bin/linux/amd64/kubectl" Please ensure that /usr/local/bin is in your search PATH, so the `kubectl` command can be found. > az aks get-credentials -g aks -n aks-cluster Merged "aks-cluster" as current context in /home/azureuser/.kube/config
For the earlier mentioned provisioning step of the cluster-admin ClusterRoleBinding use az aks get-credentials -g aks -n aks-cluster --admin to retrieve the kubeconfig credentials for bypassing AAD.