Last year Microsoft announced the Azure Monitor for containers support for on-premises Kubernetes clusters.
As I recently switched from the Docker Desktop for Mac Kubernetes single node cluster to KinD (Kubernetes in Docker), I was curious about to try out the on-premises Kubernetes cluster support.
> docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 53ea2a7b52d3 kindest/node:v1.18.2 "/usr/local/bin/entr…" 6 days ago Up 5 hours 127.0.0.1:6443->6443/tcp, 127.0.0.1:80->30000/tcp, 127.0.0.1:443->30001/tcp, 127.0.0.1:15020->30002/tcp kind-control-plane
First, we need an Azure Log Analytics workspace with the ContainerInsights solution enabled before we can connect the KinD single node cluster with Azure Monitor for containers.
This can be done via a lot of different ways like Azure Resource Manager templates, Terraform or Azure CLI. If you are using Terraform, I have a ready to go Terraform module published on my GitHub repo.
-> https://github.com/neumanndaniel/terraform/tree/master/modules/log_analytics
Preferring the Azure CLI? Just run the following two commands.
> az monitor log-analytics workspace create --resource-group {Resource_Group_Name} --name {Log_Analytics_Workspace_Name}
> az monitor log-analytics workspace pack enable --name ContainerInsights --resource-group {Resource_Group_Name} --workspace-name {Log_Analytics_Workspace_Name}
Before we can deploy the azuremonitor-containers Helm chart onto KinD we need the Log Analytics workspace id and one of the shared keys.
We get the necessary information by running the following Azure CLI commands.
> az monitor log-analytics workspace show --resource-group {Resource_Group_Name} --name {Log_Analytics_Workspace_Name} | jq -r .customerId
> az monitor log-analytics workspace get-shared-keys --resource-group {Resource_Group_Name} --name {Log_Analytics_Workspace_Name} | jq -r .primarySharedKey
Now we are ready to deploy the Helm chart. I am using Helm 3 here.
> helm repo add incubator https://kubernetes-charts-incubator.storage.googleapis.com/
> helm upgrade azuremonitor incubator/azuremonitor-containers --install --namespace kube-system \
--set omsagent.secret.wsid={Log_Analytics_Workspace_Id},omsagent.secret.key={Log_Analytics_Workspace_Primary_Key},omsagent.env.clusterName=KinD
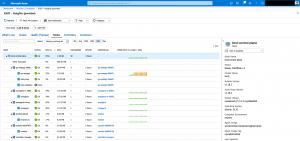
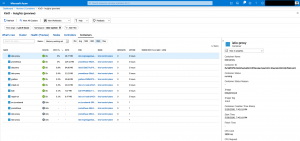
You should see now the omsagent-rs and omsagent pods in your kube-system namespace.
> kubectl get deployments omsagent-rs && kubectl get daemonsets omsagent NAME READY UP-TO-DATE AVAILABLE AGE omsagent-rs 1/1 1 1 26h NAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE omsagent 1 1 1 1 1 beta.kubernetes.io/os=linux 26h
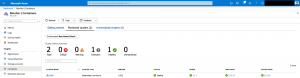
It might take a couple of minutes that the KinD single node cluster shows up in the Azure portal under Azure Monitor due to the processing of the first-time ingested data sets.
But then you get the same experience as with an Azure Kubernetes Service cluster except for the live data options like live streaming of container logs.