Digging deeper into the Azure Resource Manager capabilities and the template design I got involved today with the Azure VM Extensions. Especially with the Microsoft Monitoring Agent and the automatic configuration for Azure Operational Insights.
-> http://azure.microsoft.com/en-us/services/operational-insights/
If you are using VMs in Azure you want some monitoring and analyzing capabilities for them. Instead of depending on a hybrid network design and System Center Operations Manager you can use Operational Insights for such requirements. But do not expect the same functionality as SCOM provides you with, both products are made for different purposes. Before we start with the ARM template integration of the MMA you should have an Azure subscription with an Operational Insights workspace to test your template afterwards.
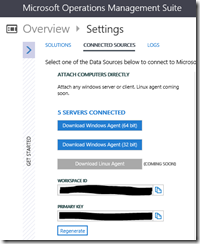
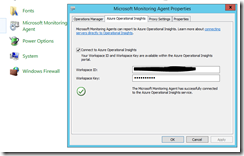
The first step is to log in into the Operational Insights workspace and write down the Workspace ID and the Primary Key under Settings.
Now you can move on. Because I am just talking about the template integration of the MMA I assume that you have a ready to use IaaS VM ARM template in which you can integrate the following lines.
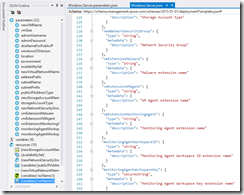
In the parameters section of the ARM template you add the following three new parameters vmExtensionMonitoringAgent, monitoringAgentWorkspaceID and monitoringAgentWorkspaceKey.
“vmExtensionMonitoringAgent”: {
“type”: “string”,
“metadata”: {
“description”: “Monitoring Agent extension name”
}
},
“monitoringAgentWorkspaceID”: {
“type”: “string”,
“metadata”: {
“description”: “Monitoring Agent Workspace ID extension name”
}
},
“monitoringAgentWorkspaceKey”: {
“type”: “securestring”,
“metadata”: {
“description”: “Monitoring Agent Workspace Key extension name”
}
}
It is really important that the parameter monitoringAgentWorkspaceKey is of the type securestring! Otherwise your primary workspace key will get exposed in the deployment history of your Resource Group.
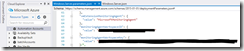
Now you create the extension resource in the resources section of the ARM template.
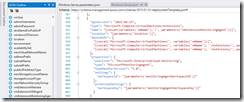
{
“apiVersion”: “2015-06-15”,
“type”: “Microsoft.Compute/virtualMachines/extensions”,
“name”: “[concat(variables(‘vmName’),’/’, parameters(‘vmExtensionMonitoringAgent’))]”,
“location”: “[parameters(‘location’)]”,
“dependsOn”: [
“[concat(‘Microsoft.Compute/virtualMachines/’, variables(‘vmName’))]”,
“[concat(‘Microsoft.Compute/virtualMachines/’, variables(‘vmName’), ‘/extensions/’, parameters(‘vmExtensionMalware’))]”,
“[concat(‘Microsoft.Compute/virtualMachines/’, variables(‘vmName’), ‘/extensions/’, parameters(‘vmExtensionVMAgent’))]”
],
“properties”: {
“publisher”: “Microsoft.EnterpriseCloud.Monitoring”,
“type”: “MicrosoftMonitoringAgent”,
“typeHandlerVersion”: “1.0”,
“settings”: {
“workspaceId”: “[parameters(‘monitoringAgentWorkspaceID’)]”
},
“protectedSettings”: {
“workspaceKey”: “[parameters(‘monitoringAgentWorkspaceKey’)]”
}
}
}
You can remove the dependencies to the other extensions I am using under dependsOn but you should not remove the dependency to the VM. The publisher name is Microsoft.EnterpriseCloud.Monitoring, the type name is MicrosoftMonitoringAgent and the type handler version is 1.0.
Another important difference to other extensions like the Microsoft Antimalware extension is the use of the protectedSettings for the primary workspace key. Normally you would define all the settings under settings but as mentioned above you do not want to expose your primary workspace key and for that reason it has to be placed under protectedSettings.
The last step is to define the values for the parameters in the template parameter file.
“vmExtensionMonitoringAgent”: {
“value”: “MicrosoftMonitoringAgent”
},
“monitoringAgentWorkspaceID”: {
“value”: “WorkspaceID”
},
“monitoringAgentWorkspaceKey”: {
“value”: “WorkspaceKey”
}
If you do not want to define your Workspace ID and Workspace Key in a template parameter file you can add them as parameters to the New-AzureResourceGroupDeployment cmdlet. But then you should define the template parameter file with the following values.
“vmExtensionMonitoringAgent”: {
“value”: “MicrosoftMonitoringAgent”
},
“monitoringAgentWorkspaceID”: {
“value”: “”
},
“monitoringAgentWorkspaceKey”: {
“value”: “”
}
You can now start the deployment to Azure with the Azure Resource Manager PowerShell cmdlets.
Deployment type 1 included in the template parameter file:
$Credential=Get-Credential
New-AzureResourceGroupDeployment -ResourceGroupName $ResourceGroupName -TemplateFile “C:VolumeOneDriveSyncAzureARMProductionCPWindows.Server.json” -adminUsername $Credential.UserName -adminPassword $Credential.Password -TemplateParameterFile “C:VolumeOneDriveSyncAzureARMProductionCPWindows.Server.parameters.json” –Verbose
Deployment type 2 outside the template parameter file:
$Credential=Get-Credential
New-AzureResourceGroupDeployment -ResourceGroupName $ResourceGroupName -TemplateFile “C:VolumeOneDriveSyncAzureARMProductionCPWindows.Server.json” -adminUsername $Credential.UserName -adminPassword $Credential.Password –monitoringAgentWorkspaceID $WorkspaceID –monitoringAgentWorkspaceKey $WorkspaceKey -TemplateParameterFile “C:VolumeOneDriveSyncAzureARMProductionCPWindows.Server.parameters.json” –Verbose
After the deployment completes successfully you can now log in into the VM and have a look if the Microsoft Monitoring Agent was installed and configured correctly.
As you can see it everything is fine and you should see as soon as possible some data in your Operational Insights workspace.