Jenkins has two nifty plugins available to leverage the power of the Azure platform for on-demand worker nodes.
-> Azure Container Instances
-> Azure Virtual Machines
In this blog post I want to quickly highlight to secure the access to Jenkins worker nodes running on Azure.
The assumption is that your Jenkins CI master is running outside of Azure e.g. on-premises.
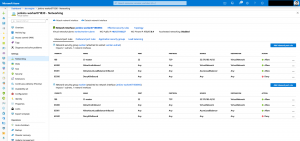
When you are using the Azure VM Agents plugin with its default configuration, every new Jenkins worker node on Azure gets its own public IP address without a NSG attached to it.
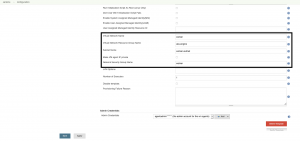
Now there are two ways to mitigate that. First, implementing a S2S VPN connection between the Jenkins CI master and the worker nodes. But that requires to create a Virtual Network upfront for the worker nodes and connect the Virtual Network to the VPN. Furthermore, set the following settings in the plugin configuration to utilize the solution. Especially check mark Make VM agent IP private.
This ensures that the Jenkins worker nodes are deployed without a public IP address and are therefore only reachable over the S2S VPN connection.
If a S2S VPN connection is not an option, then there is an alternative way making the communication more secure.
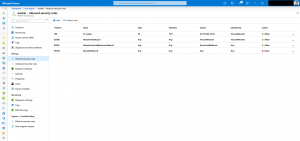
Same as with the first option you create the Virtual Network upfront. Additionally, a NSG is created as well before. The NSG gets then attached to the subnet of the Virtual Network.
In this scenario the Jenkins worker nodes have a public IP address. So, we restrict the inbound access to the worker nodes with the NSG. Only one inbound rule is created for the SSH TCP port 22.
The source should be restricted to the public IP address of the Jenkins CI master to enable only inbound access from the CI master itself.
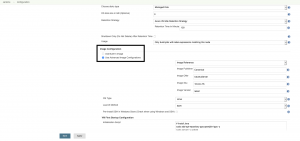
Finally, we set the configuration in the Azure VM Agents plugin and the Jenkins worker nodes are secured compared to the default settings.