Microsoft Defender for Cloud supports the continuous export of a variety of data to Azure Event Hubs and Azure Log Analytics workspaces. When you use Azure Event Hubs, you can stream those data also to 3rd-party solutions or Azure Data Explorer. The continuous export is handy for security alerts to maintain them for a longer period than the default 90 days.
Using the Azure portal to configure the continuous export functionality is straightforward, but it gets cumbersome when configuring it for multiple subscriptions.
Infrastructure as code
Here comes infrastructure as code into play to automate the configuration in a well-defined way. In our example, we use Terraform and the azurerm_security_center_automation resource to export security alerts to a Log Analytics workspace.
data "azurerm_client_config" "current" {
}
resource "azurerm_security_center_automation" "continuous_export" {
name = var.name
location = var.location
resource_group_name = var.resource_group_name
enabled = true
action {
type = "loganalytics"
resource_id = var.log_analytics_workspace_id
}
source {
event_source = "Alerts"
rule_set {
rule {
property_path = "Severity"
operator = "Equals"
expected_value = "high"
property_type = "String"
}
}
rule_set {
rule {
property_path = "Severity"
operator = "Equals"
expected_value = "medium"
property_type = "String"
}
}
rule_set {
rule {
property_path = "Severity"
operator = "Equals"
expected_value = "low"
property_type = "String"
}
}
}
scopes = ["/subscriptions/${data.azurerm_client_config.current.subscription_id}"]
}
We provide the Terraform module with the required inputs and apply those configuration changes.
module "microsoft_defender_continuous_export" {
source = "../modules/microsoft_defender_continuous_export"
name = "continuous-export"
resource_group_name = "continuous-export-config"
location = "northeurope"
log_analytics_workspace_id = "/subscriptions/<subscription_id>/resourceGroups/operations-management/providers/Microsoft.OperationalInsights/workspaces/sentinel-sec"
}
Afterward, we have a look into the Azure portal and see that the export object gets created. However, the settings page for the continuous export still represents an unconfigured continuous export.
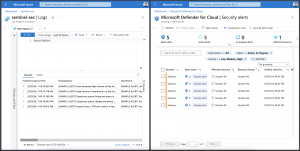
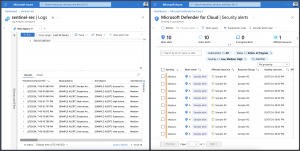
Does our configuration actually work? The answer is yes, and triggering demo alerts, for instance, for Azure Key Vault, provides the proof.
As seen in the screenshot above the security alerts got exported to the Log Analytics workspace.
Make continuous export configuration visible
There is still the question of why the settings page shows an unconfigured continuous export. First, we can configure multiple continuous exports for Microsoft Defender for Cloud on a subscription with different targets, for instance, different Log Analytics workspaces. Second, the settings page expects a specific name for the configuration, and the name is ExportToWorkspace.
Now we know how to make the configuration visible in the Azure portal on the settings page.
module "microsoft_defender_continuous_export" {
source = "../modules/microsoft_defender_continuous_export"
name = "ExportToWorkspace"
resource_group_name = "continuous-export-config"
location = "northeurope"
log_analytics_workspace_id = "/subscriptions/<subscription_id>/resourceGroups/operations-management/providers/Microsoft.OperationalInsights/workspaces/sentinel-sec"
}
Applying the adapted Terraform module deletes the former export object and creates a new one with the name ExportToWorkspace.
The configuration is now visible. Again, we trigger demo alerts to verify our configuration.
Summary
When configuring the continuous export of Microsoft Defender for Cloud for a subscription, you should use the name ExportToWorkspace or ExportToHub. Using the expected names ensures that the default continuous export configuration is visible in the Azure portal on the settings page. Additional continuous export configurations can have a different name and are fully functional besides the default continuous export configuration.
You can find the Terraform module on my GitHub repository.
-> https://github.com/neumanndaniel/terraform/tree/master/modules/microsoft_defender_continuous_export