Running an ingress controller on Azure Kubernetes Service requires configuration of the Azure Traffic Manager endpoint monitoring options when Traffic Manager is used in front of it.
In this blog post I will show you an example configuration of the Traffic Manager endpoint monitoring for a container application behind the Ambassador API gateway running on AKS.
First, here is the Kubernetes service object configuration of the Ambassador API gateway.
apiVersion: v1
kind: Service
metadata:
labels:
service: ambassador
name: ambassador
annotations:
service.beta.kubernetes.io/azure-dns-label-name: azst-aks1-ambassador
spec:
type: LoadBalancer
externalTrafficPolicy: Local
ports:
- port: 80
targetPort: 80
selector:
service: ambassador
The specialty in this configuration is the Azure DNS label name annotation. We need this annotation since otherwise we cannot select the Azure Public IP as an Azure endpoint in Azure Traffic Manager.
Next let us have a look at the Kubernetes service object configuration of the container application.
apiVersion: v1
kind: Service
metadata:
name: go-webapp
labels:
app: go-webapp
annotations:
getambassador.io/config: |
---
apiVersion: ambassador/v1
kind: Mapping
name: go-webapp
prefix: /
host: aks.trafficmanager.net
service: go-webapp.default.svc.cluster.local
add_request_headers:
l5d-dst-override: go-webapp.default.svc.cluster.local:80
spec:
ports:
- port: 80
targetPort: 8080
selector:
app: go-webapp
In the Ambassador configuration annotation, I am specifying as host the Azure Traffic Manager URL / DNS name.
When we now look at the Traffic Manager endpoint the monitor status is in degraded state instead of online. The reason for that is the missing configuration adjustment to the Traffic Manager endpoint monitoring.
Without any adjustment the endpoint monitoring targets directly the Ambassador installation as ingress controller and Ambassador returns per default the 404 HTTP code. The endpoint monitoring does not contain a specific hostname in the customer header in this case. Therefor Ambassador does not know to which container application in the Kubernetes cluster it should forward the endpoint monitoring request.
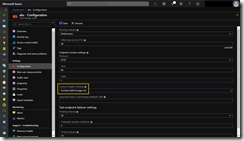
Solving this issue just click onto the Configuration tab and set the hostname under Custom Header settings.
host:aks.trafficmanager.net
Shortly after hitting the Save button the Traffic Manager endpoint changes its monitor status to online.
Keep in mind that depending on the configuration how the ingress controller publishes the container application, the Azure Traffic Manager endpoint monitoring configuration might be different to the example I showed you in this blog post.