Earlier this year Microsoft has launched a new Azure service for network diagnostics and troubleshooting called Network Watcher.
-> https://azure.microsoft.com/en-us/services/network-watcher/
The Network Watcher offers a range of tools like VPN diagnostics and packet capturing to mention two of them. But I would like to talk about the VPN diagnostics capability in this blog post.
Before we can use the VPN diagnostics, we have to enable the Network Watcher for the specific region.
There is only one Network Watcher instance per Azure region in a subscription.
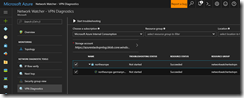
For the next step we jump into the VPN Diagnostics section and selecting our desired VPN gateway with the corresponding connection. We also have to select a storage account to store the generated log files.
Before we kick off the diagnostic run, we have to make sure that the VPN gateway type is supported by the Network Watcher! Currently, only route-based VPN gateway types are supported.
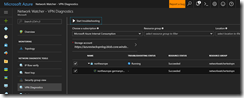
Now we can start the diagnostic run with a click on Start troubleshooting.
For downloading the log files, I am using the Azure Storage Explorer.
-> http://storageexplorer.com/
The log files are sorted by date and time of the latest run and will be placed in a .zip file.
Our first run was a healthy one. So the .zip file contains two files.
ConnectionStats.txt
Connectivity State : Connected
Remote Tunnel Endpoint :
Ingress Bytes (since last connected) : 10944 B
Egress Bytes (Since last connected) : 10944 B
Connected Since : 6/28/2017 7:01:49 AM
CPUStat.txt
Current CPU Usage : 0 %
Current Memory Available : 595 MBs
To force a run that shows the VPN gateway in an unhealthy state, I have edited the PSK on one side. So the PSK does not match anymore.
Now we get additional files with the .zip file. Beside the ConnectionStats.txt and the CPUStat.txt, we got IKEErrors.txt, Scrubbed-wfpdiag.txt, wfpdiag.txt.sum and wfpdiag.xml. The most important ones are IKEErrors.txt and Scrubbed-wpfdiag.txt.
IKEErrors.txt
Error: Authenticated failed. Check keys and auth type offers.
based on log : Peer sent AUTHENTICATION_FAILED notify
Error: Authentication failed. Check shared key. Check crypto. Check lifetimes.
based on log : Peer failed with Windows error 13801(ERROR_IPSEC_IKE_AUTH_FAIL)
Error: On-prem device sent invalid payload.
based on log : IkeFindPayloadInPacket failed with Windows error 13843(ERROR_IPSEC_IKE_INVALID_PAYLOAD)
Scrubbed-wfpdiag.txt
…
[0]0368.0D7C::06/28/2017-11:46:45.651 [ikeext] 13|51.5.240.234|Failure type: IKE/Authip Main Mode Failure
[0]0368.0D7C::06/28/2017-11:46:45.651 [ikeext] 13|51.5.240.234|Type specific info:
[0]0368.0D7C::06/28/2017-11:46:45.651 [ikeext] 13|51.5.240.234| Failure error code:0x000035e9
[0]0368.0D7C::06/28/2017-11:46:45.651 [ikeext] 13|51.5.240.234| IKE authentication credentials are unacceptable
…
The IKEErrors.txt file gives us an overview what maybe wrong and we can start checking those settings. For a better troubleshooting in more details we have to take a look into the Scrubbed-wfpdiag.txt file. As quoted out from the file we got the exact information that something is wrong with the provided credentials also known as our PSK.
As you can see the Network Watcher is an easy to use SaaS service providing you with the necessary tool set to diagnose and troubleshoot network issues and misconfigurations in your Azure environment.